Altay is an industry analyst at AIMultiple. He has background in international political economy, multilateral organizations, development cooperation, global politics, and data analysis.
We follow ethical norms & our process for objectivity. Brands with links to their websites fund our research.
Application security is significant for businesses, with at least one vulnerability found in over 75 percent of applications, making them susceptible to cyber threats. An application risk assessment is a systematic process designed to identify, analyze, and manage potential security risks in software applications.
This crucial component of application security risk management aims to uncover vulnerabilities or weaknesses within an application’s architecture, code, or operational environment that could be exploited by cyber attackers. This article provides a detailed view of the application risk assessment checklists, best practices, and challenges.
An application risk assessment is a comprehensive process to evaluate and understand the security risks associated with a particular application or set of applications. This involves identifying potential vulnerabilities and threats and assessing their possible impact on the application’s security and functionality. The goal is to inform the development of a risk management plan or provide specific recommendations to IT or security teams to enhance the application’s security posture.
The benefits of conducting application risk assessments include:

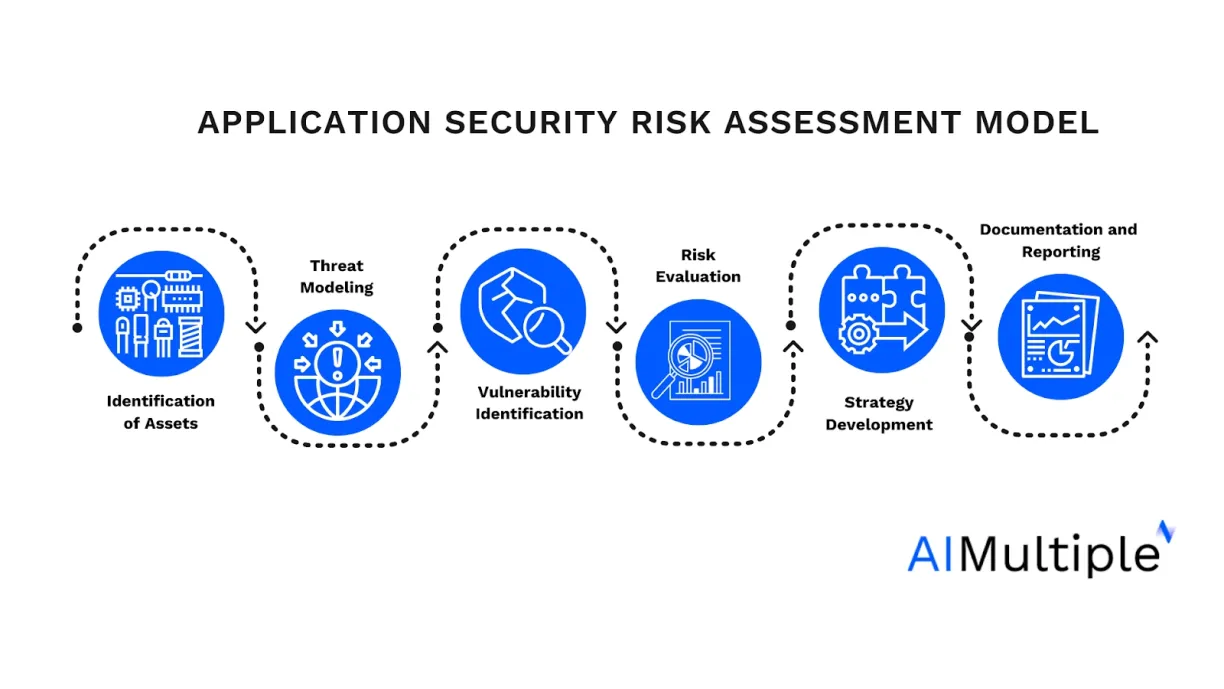
This is the cornerstone of your risk assessment, focusing on pinpointing the crucial elements that your application relies on. This involves a process of listing all components, such as:
Each asset is then carefully evaluated to understand its significance and sensitivity, thereby establishing a clear priority list. This step is essential for grasping what exactly needs protection and how each component contributes to your application’s overall functionality and objectives.
This step advances the process by systematically identifying potential threats to these critical assets. It involves a deep dive into the application’s architecture, including:
This stage is about envisioning how an adversary could potentially compromise your application by considering different threat agents and constructing possible attack scenarios. The aim is to adopt an attacker’s mindset to uncover all conceivable vulnerabilities that could be exploited.
Vulnerability identification follows as a natural progression, where the focus shifts to identifying specific weaknesses within the application that could be leveraged by threats. Employing a combination of automated vulnerability scanning tools, expert code reviews, and controlled penetration tests helps in covering these vulnerabilities.
Automated tools are adept at spotting known issues in code and configurations, while manual reviews and tests simulate real-world attacks to identify hidden weaknesses that automated tools might overlook. Refer to our articles to gain a comprehensive understanding of each:
Risk evaluation is a critical phase where each identified vulnerability is assessed to determine its risk level. This involves evaluating the likelihood of a vulnerability being exploited, considering factors like exploit complexity and the attacker’s required skill level.
The potential impact of an exploit is also assessed, considering the possible consequences such as data breaches, financial losses, or damage to reputation. Based on these evaluations, risks are prioritized to ensure that mitigation efforts are focused where they are most needed.
This step involves deciding on the best course of action to manage the identified risks. This could involve direct fixes to vulnerabilities, transferring the risk through insurance, accepting the risk when mitigation costs outweigh potential impacts, or implementing additional controls to reduce risk when direct mitigation isn’t feasible. The chosen strategies are tailored to address the identified vulnerabilities and risks, focusing on preserving the application’s security and functionality.
This step encapsulates the entire risk assessment process, providing a detailed record of identified assets, threats, vulnerabilities, risks, and the strategies planned or implemented to mitigate them. This documentation serves as a vital tool for tracking and managing risk over time and ensures compliance with industry regulations, facilitating decision-making, and demonstrating due diligence in risk management.
Today’s applications often have complex architectures, use multiple third-party components, and are deployed across various environments (cloud, on-premises, hybrid). This complexity makes it difficult to identify all potential vulnerabilities and assess the entire attack surface.
The fast pace of technological advancements and the continuous evolution of cyber threats mean that risk assessment processes must be dynamic and adaptable. Staying current with new vulnerabilities, attack techniques, and mitigation strategies is challenging.
Many organizations face limitations in terms of budget, time, and skilled personnel dedicated to cybersecurity. This can hinder the thoroughness and frequency of application risk assessments, potentially leaving vulnerabilities unaddressed.
Integrating security assessments into the software development lifecycle (SDLC) without slowing development processes is challenging. Balancing speed and security in agile and DevOps environments requires careful planning and tool integration.
The regulatory landscape for data compliance, protection and cybersecurity is constantly evolving. Ensuring that risk assessments cover all relevant compliance requirements and that mitigation strategies align with these regulations can be complex and time-consuming.
Effectively integrating threat intelligence into the risk assessment process to understand the latest threats and vulnerabilities facing similar applications or industries is challenging. This requires access to up-to-date threat intelligence and the ability to contextualize and apply this information to the specific application environment.
Performing security risk assessments is crucial because it helps identify vulnerabilities and weaknesses in applications that could be exploited by attackers. It ensures that security risks are managed proactively, thereby protecting sensitive data and maintaining trust with users.
Ideally, a team with a mix of skills including application development, cybersecurity, and network security should conduct the assessment. External security consultants or specialized security firms can also be engaged for an unbiased and thorough assessment.
Common methodologies include threat modeling, static application security testing (SAST), dynamic application security testing (DAST), and penetration testing. Each method provides a different perspective on application security, and a combination is often used for a comprehensive assessment.
The frequency of assessments depends on several factors such as the application’s criticality, the environment it operates in, regulatory requirements, and changes to the application or its operating environment. Generally, it’s recommended to perform assessments at least annually or after significant changes to the application.
While automated tools can identify many common vulnerabilities and weaknesses, they cannot replace the need for expert analysis, especially for complex applications and sophisticated threat vectors. A combination of automated tools and expert review is typically the most effective.
Findings should be prioritized based on their risk level, and a remediation plan should be developed to address each identified vulnerability. High-risk vulnerabilities should be addressed immediately, while lower-risk ones can be scheduled for future remediation based on available resources.
It is a critical component of a holistic security strategy, ensuring that applications are not the weakest link in an organization’s security posture. It complements other security practices such as network security, incident response, and security awareness training.
Yes, several standards and frameworks can guide the assessment process, including the Open Web Application Security Project (OWASP) Testing Guide, NIST Special Publication 800-53, and ISO/IEC 27001. These provide best practices and methodologies for conducting thorough and effective security assessments.
If you have further questions, reach us: